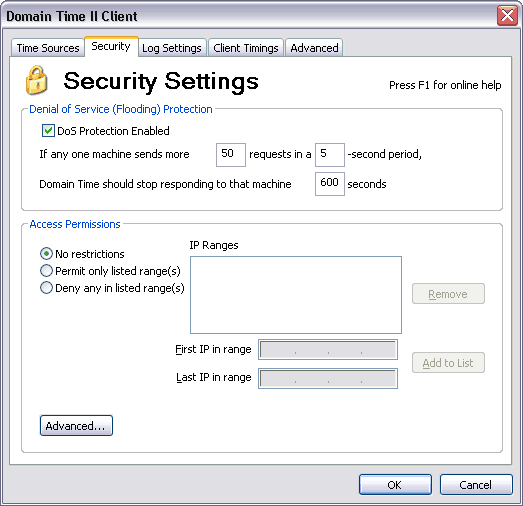
 Full Client Control Panel Applet - Security Settings Tab Denial of Service (Flooding) Protection Automatic protection against Denial of Service (DoS) attacks.
DoS Protection Enabled
If any one machine sends more than requests in a -second period, The default settings should be sufficient for most applications, however, you may wish to adjust them if you have different traffic security requirements. Control which machines can communicate with your client.
To prevent this kind of problem, you may specify whether Domain Time should accept or reject time protocol traffic from certain IP addresses. You can specify whether to Permit or Deny traffic from multiple ranges of addresses. This allows you to easily restrict your time traffic to come only from the systems you intend. If you wish to permit or deny a single IP address, enter it as both the First and Last IP address in the range. No restrictions is the default setting. These values can also be preset using the DOMTIME.INI template file. Advanced - Command Restrictions When you click on the Advanced button on the Security tab, you'll be presented with the Command Restrictions dialog window. You can use these settings to restrict what kind of Domain Time II control and sync messages your client listens for on the network.
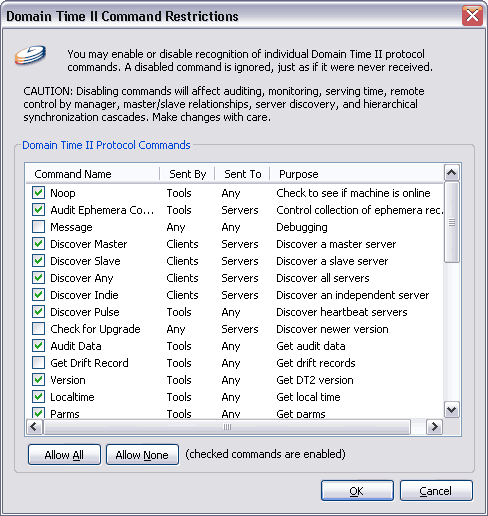 The Domain Time II Full Client - Command Restrictions Page The default protocol restriction settings assure both maximum functionality and a high degree of security; in most cases you will have no need to adjust them from the defaults. Domain Time II components communicate with each other primarily through directed communication, and are therefore highly resistant to spoofing and malign interference. The Domain Time II protocol command restriction capability is intended for use by system administrators in environments where an extra level of security is required, such as running a Client on the open Internet. Using the restrictions list, you can determine exactly what Domain Time II protocol command messages the service is allowed to listen for. Think of the command restriction list as an application-level "firewall" allowing in only the desired Domain Time II commands and blocking any others. Keep in mind that the restriction list only affects incoming DTII protocol commands - outgoing commands are not affected.
Warning:
|